Safe. Secure. Authenticated.
A straightforward solution for secure connectivity you can trust.
Our solution
A unique challenge
Each industry faces unique challenges and risks associated with connected devices. For example, unauthorized access to connected medical devices can pose serious risks for patient safety and privacy. Connected vehicles are susceptible to cyber-attacks that could compromise braking, steering and acceleration controls. Any compromise in defense and aerospace systems can have catastrophic consequences. In the supply chain, counterfeit components could risk the integrity and security of the entire device.
Cost-effective and scalable
There are millions if not billions of connecting devices.The interconnected nature of these devices poses a risk of cascading security breaches, where compromising one device means endangering entire systems, also known as Break-one = Break-all.
The current security solutions cannot keep up with the rapid expansion of the number of devices in the Internet of Things and are often costly and complex. A fully secured connected world can only be realized by a solution that is straightforward, cost-effective and will detect any infringement, counterfeit, or hacking.
Straightforward. Effective.
Trusted identity
Trusted identity refers to the establishment and verification of the legitimacy of devices, users, applications, and even the infrastructure itself. Authentication is the first line of defense, making sure that only authorized and authenticated entities can interact with IoT devices and systems. Devices must have a trusted identity to ensure they are recognized and authorized to communicate. It is at the lowest part of connected networks (end-nodes) where the trouble begins as it is hard to establishing a trusted identity at these points. This makes the end-nodes one of the most vulnerable parts of the Internet-of-Things and where hackers will strike first.
Optimised protection with both Hardware and Software
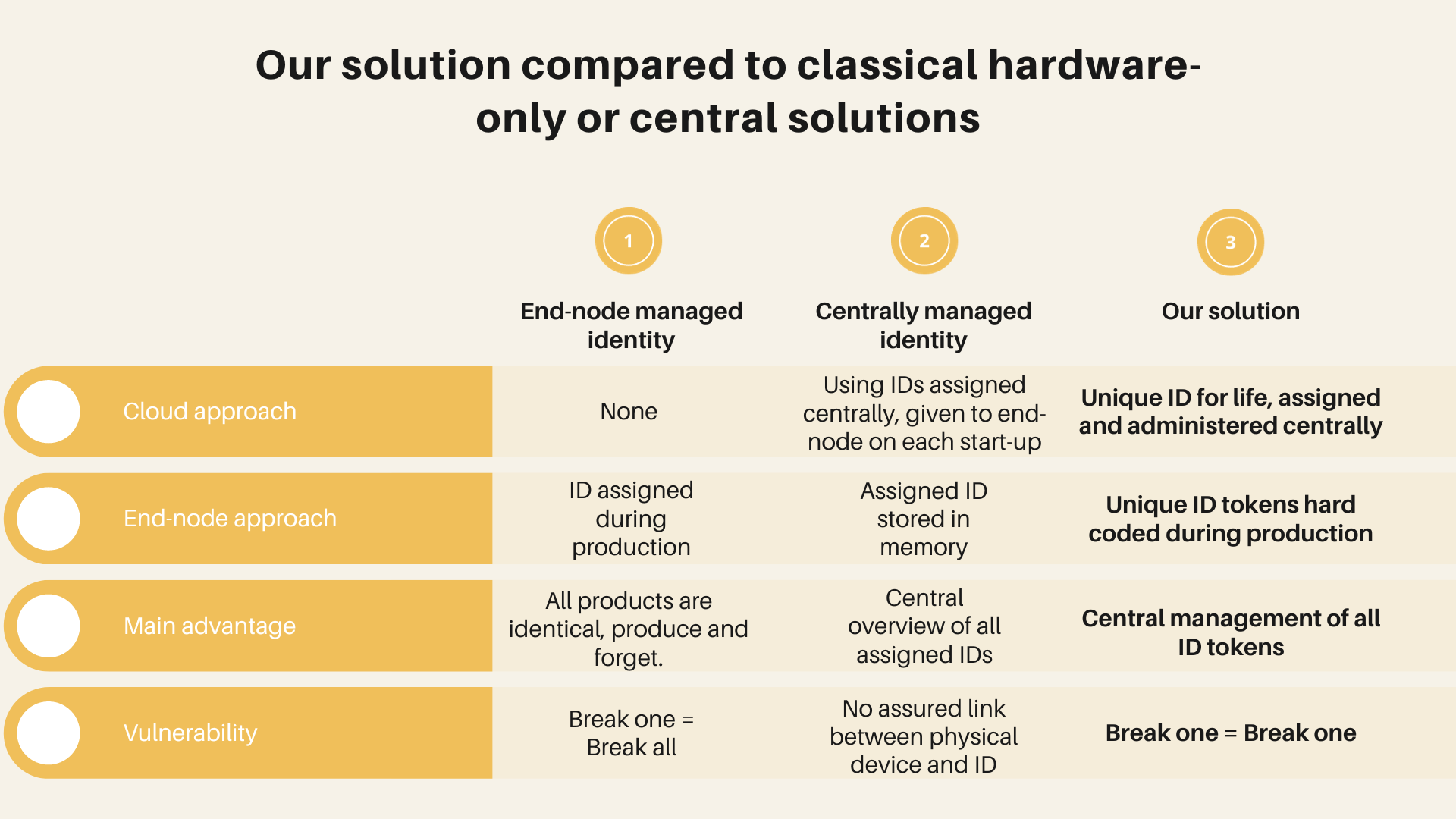
Our solution is an authentication system that relies on two key protections: a hardware token attached to the electronic components and a secure cloud.

Hardware tokens provide much higher protection and reduce the chance of any malware accessing the token. Hardware tokens are assigned, enabled, disabled, and configured from a dedicated, secure, cloud environment.
Combining the best of both worlds
Sandgrain Secured: Dual protection with hardware and software.
Hardware tokens provide much higher protection and reduce the chance of any malware accessing the token. Hardware tokens are assigned, enabled, disabled, and configured from a dedicated, centralised, cloud platform. This Cloud platform performs all secure operations and software services.
Easy to implement
Requires only tokens and a pay per use cloud platform
Scalable
Hundreds, millions to billions of tokens can be attached to IoT devices.
Trustworthy
Any infringement, counterfeit or hacking will be detected
Secure authentication of end-nodes at high volume
The most urgent need for solid authentication is for connected devices and systems within the Internet of Things. The closer to the end-nodes of the network, the more crucial it becomes. End-nodes are where hacking takes place.
There are many software solutions addressing this issue based on trusted software certificates. With proper identity checks these systems store an ID into the device memory, combined with the user password. This has a major drawback for connected devices: it lacks a link between the ID and the physical device. For example, if the ID is stored on the SIM card of a phone, all is needed is another phone and the passcode. A secure authentication, therefore, requires a physical attachment of the ID to the connected device.
Our solution provides a revolutionary solution to the challenge of securing IoT devices (end-nodes) with a simple system and at very low cost.
SandGrain will have its unique ID per IC based on a hard-coded hardware solution, providing higher reliability and robustness to hacking at significant lower cost.! Integration with a secure cloud platform ensures absolute authentication.
Offering the necessary level of protection for millions of devices is possible with the unique hardware and software combination.
Simple. Secure. Scalable.
A simple token authenticated by HSM-Cloud
Take security to the next level for all your devices connected to the Internet of Things with limitless scalability.
Unique IC token
Unique, immutable SandGrain IC-token with a hard-coded identity establishing a solid link between the identity and the device it belongs to.
HSM-Cloud:
Cloud-based data management system administers all identities and is thus able to detect any system abuse on the level of individual end node devices.
Cyber Security Authentication
Authenticating the IC-token that is attached to the device with our cloud platform

